Build, test, and optimize automated risk strategies across the entire customer lifecycle with AI-driven insights and real-time data.


















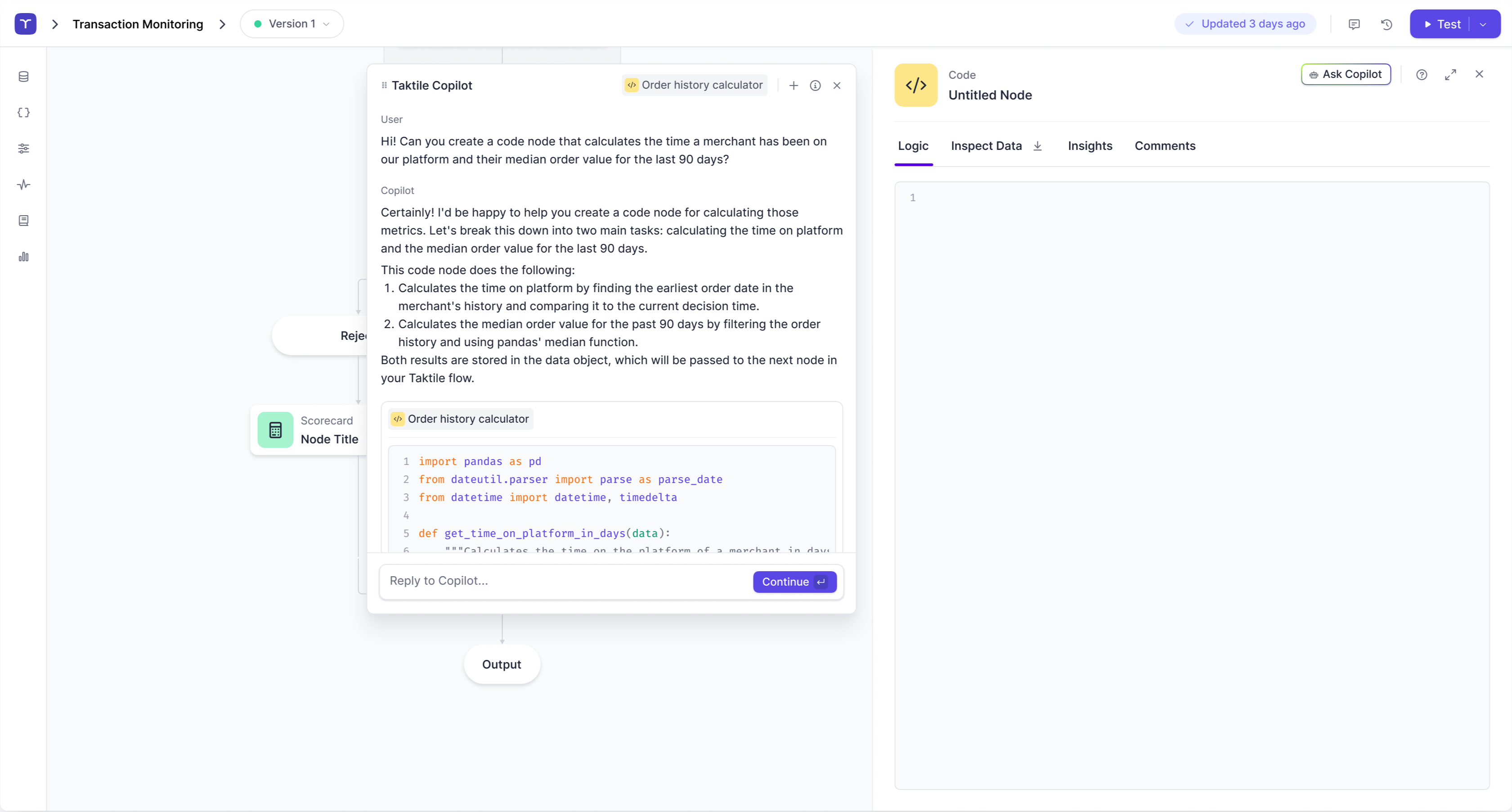
Build, manage, and optimize risk decisions with ease—regardless of technical expertise. Use Taktile's no-code features to design decision logic or leverage our AI Copilot to work with complex logic written in code.
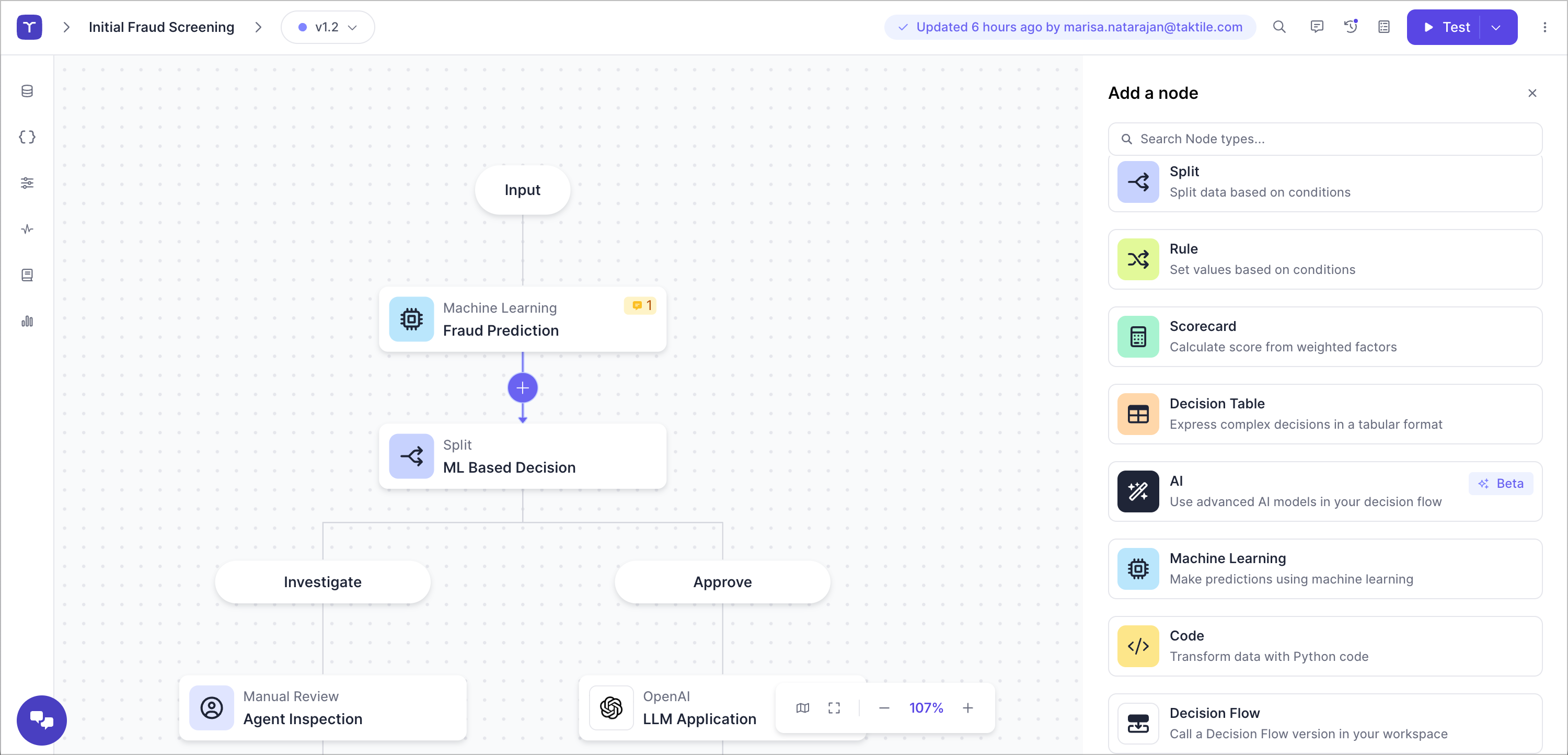
Use no-code features to design decision logic without any help from engineering.
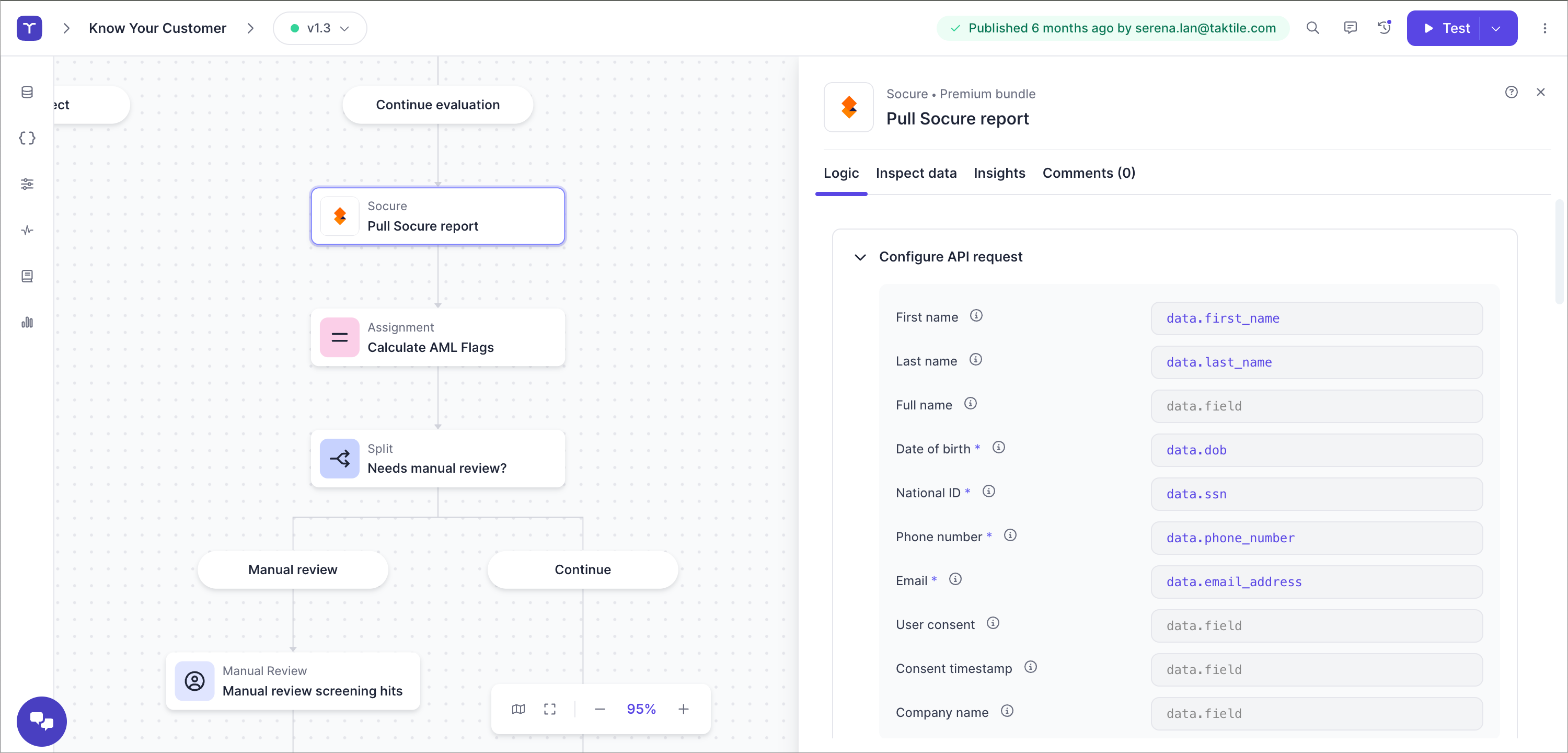
Start experimenting with new signals in your decision flows through Taktile's off-the-shelf integrations.
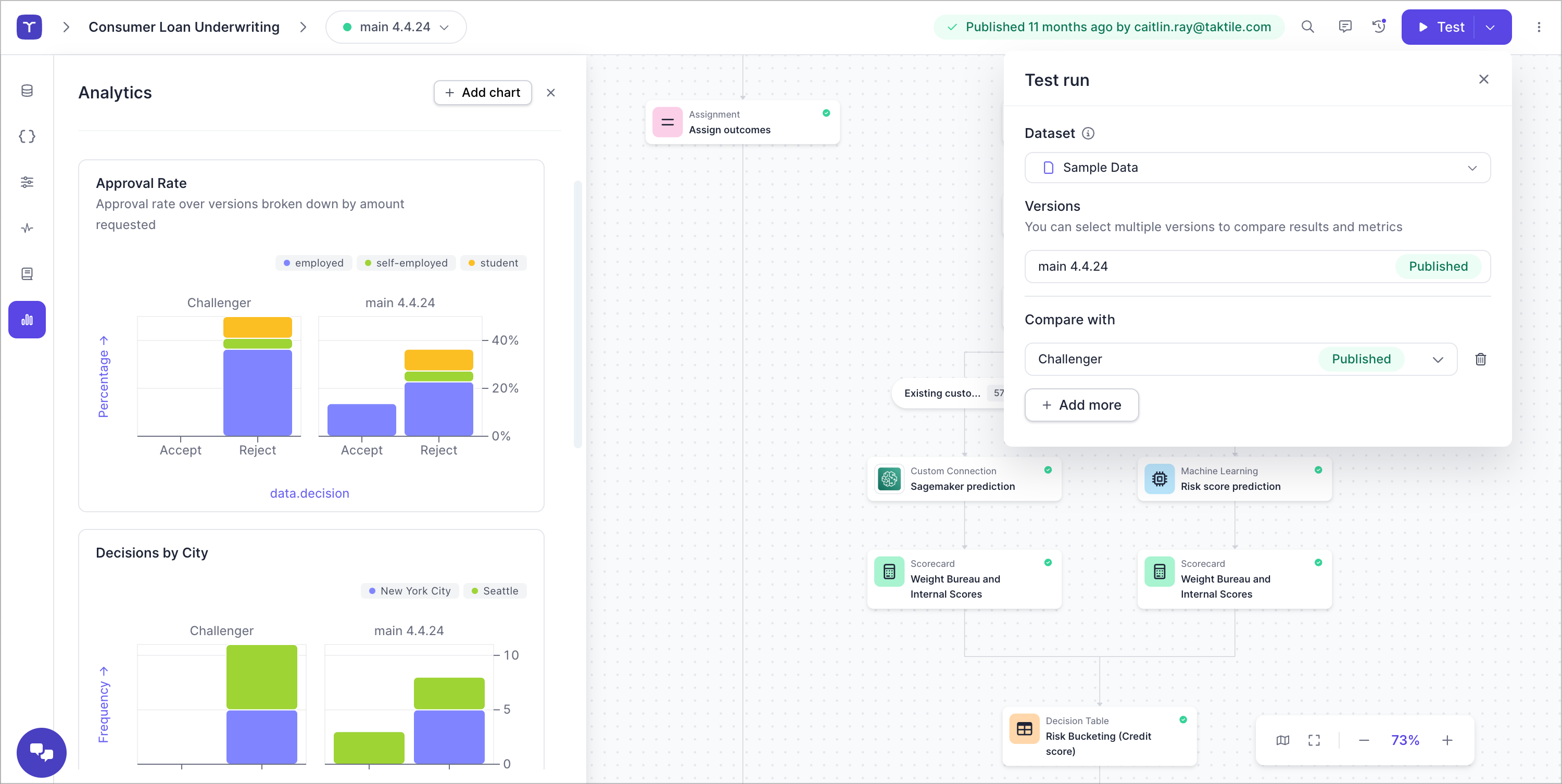
Validate the impact of every change on real-world data before rolling it out.
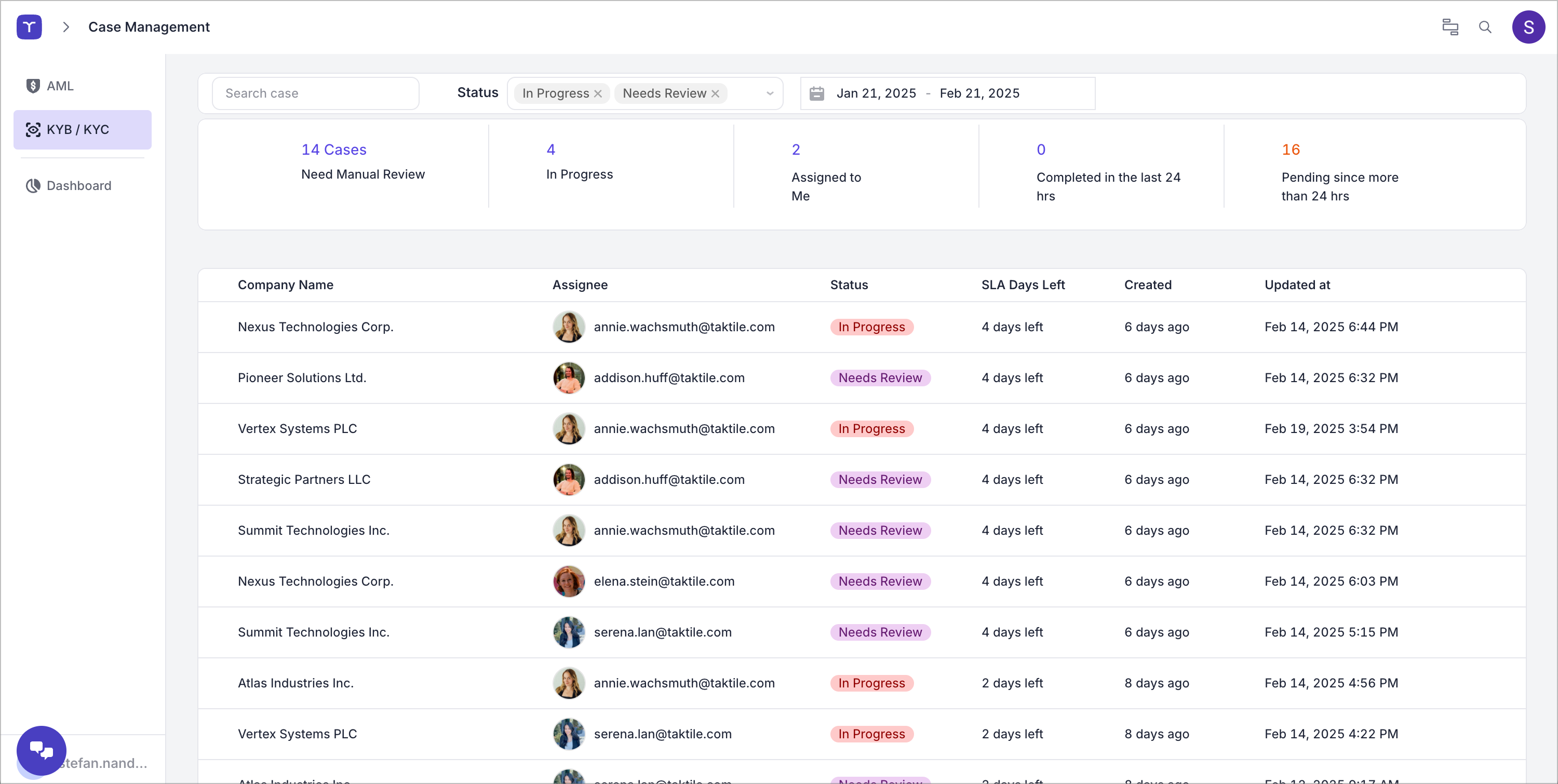
Gain full control over the information your team receives to review cases.
Use AI Copilot to generate, understand, and debug complex logic written in code.
Find any data source you need to fuel your risk decision workflows.


“It was clear that we needed a partner who fully understood the nuances of decisioning in various use cases and industries, the challenges that come with off-the-shelf AI models, and who could provide the required infrastructure to deploy LLMs in mission-critical workflows. We met Taktile just at the right time.”



AI-powered decisioning, Copilot intelligence, and AI Agent automation—built for risk teams. Enhance your risk management strategies across the entire lifecycle with AI-driven precision.
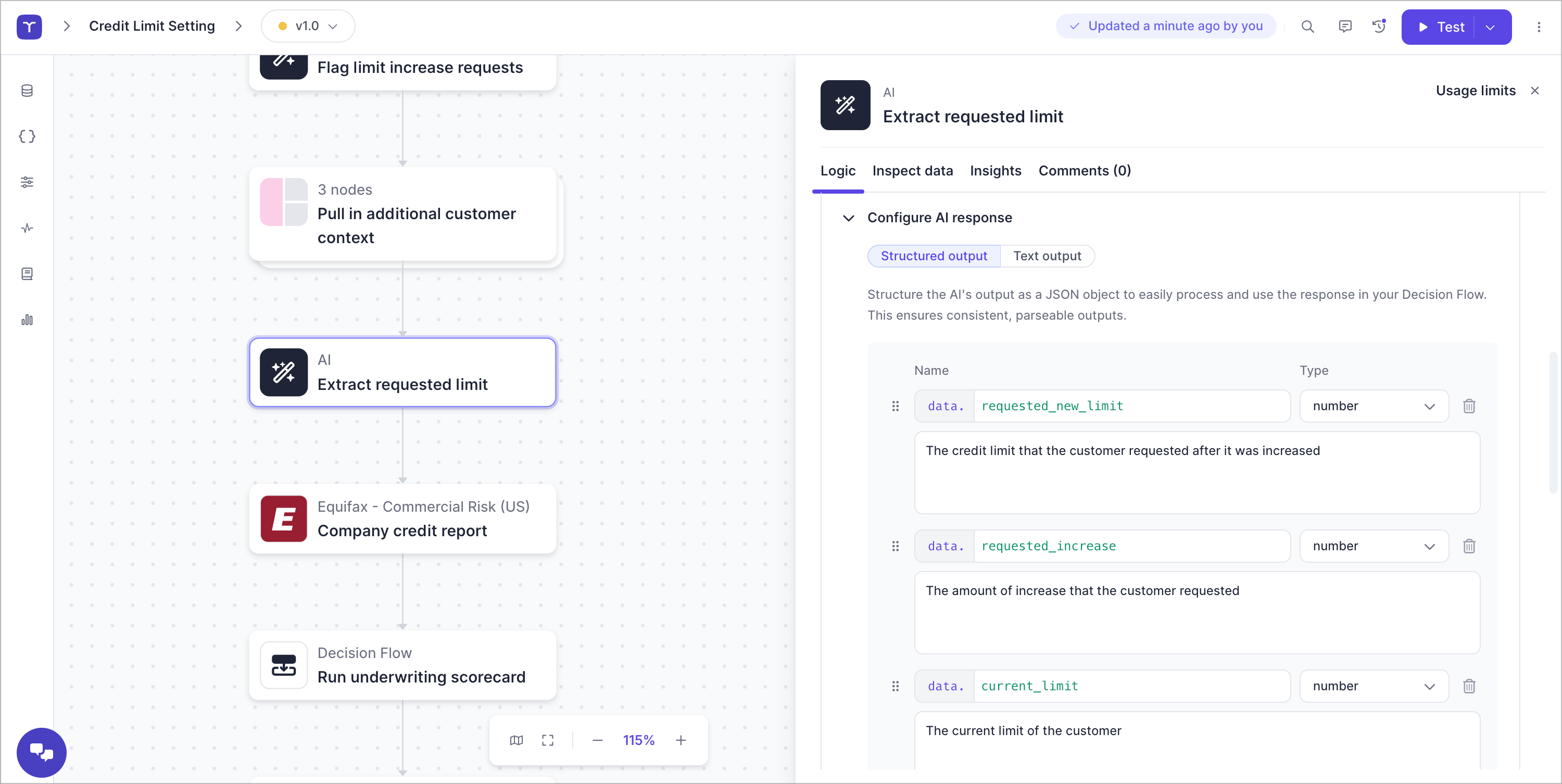
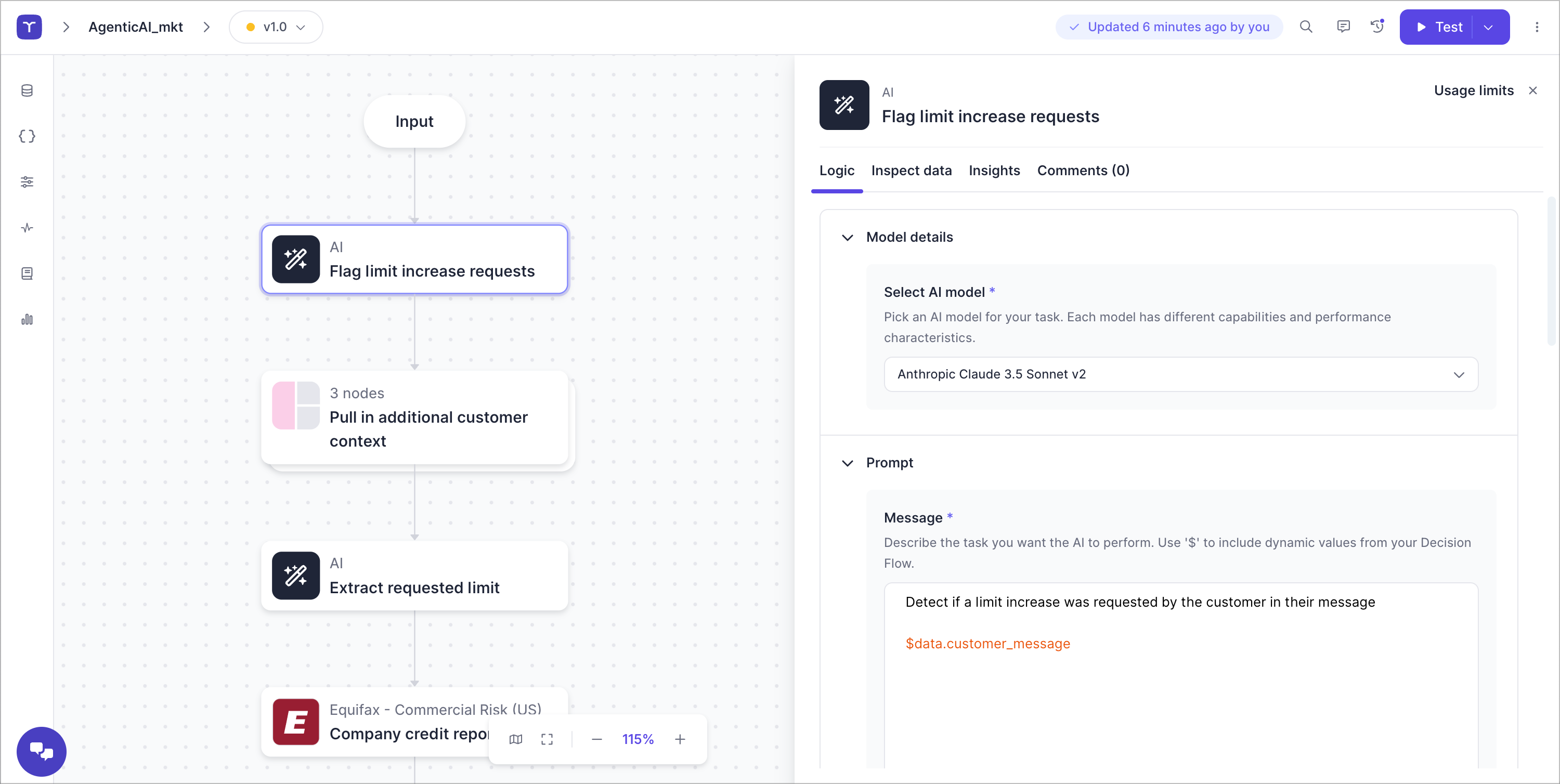

Since we allow decision authors to execute code on our infrastructure, we have invested in robust separation between customers, both for compute and storage.
Data that is captured, stored or processed by Taktile is encrypted when in transit over public networks or at rest. Specifically, we encrypt data that is transmitted over public networks using Transport Layer Security (TLS 1.2).
Taktile's services are entirely run in the cloud, meaning we do not operate or maintain our own servers. All data centers are in compliance with the highest industry standards including SOC 2 Type II and ISO 27001.
We connect to customers’ single sign on providers (SSO) and do not manage credentials. This allows customers to reuse their own authentication provider and automatically enforce their own security controls such as password complexity requirements and two-factor authentication (2FA).



